Brian Gongol
What is Phishing?
"Phishing" is a criminal method of trying to get the victim to turn over private information like passwords and account numbers by fooling them into believing that the message is being sent from a trusted source.
How to Recognize Phishing
Two things make phishing especially evil:
- Phishing disrupts the extremely important networks of trust that allow a healthy, free nation, society, and economy to function.
- Phishing disproportionately takes advantage of new and inexperienced users of the Internet.
The Original Message
On the surface, the original message looks authentic. It contains eBay logos and plenty of language intended to make the reader believe that it's a legitimate request. DON'T BELIEVE IT. What appears below is a CRIMINAL PHISHING ATTEMPT:

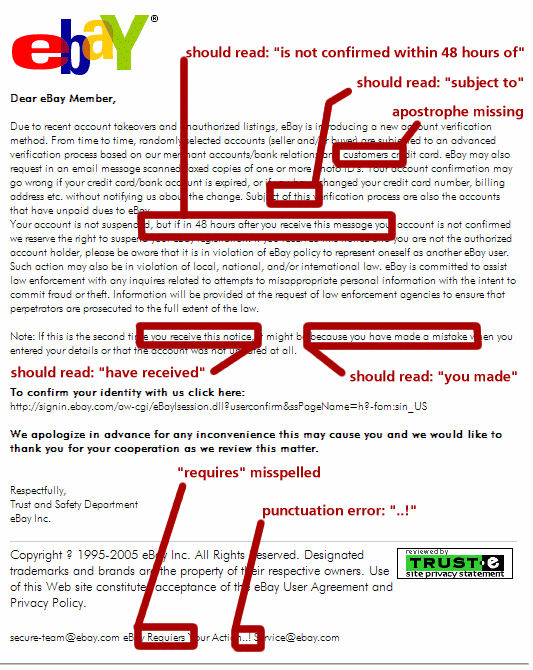
Warning Sign #1: Significant Mechanical Errors
Read the message closely. A professional service like eBay pays people to edit the messages the company sends. It's a basic matter of professionalism. But this phishing attempt includes some serious grammatical, spelling, and mechanical errors. This is typical of many phishing attempts, in part because many of them come from overseas and are written by non-native speakers of English.
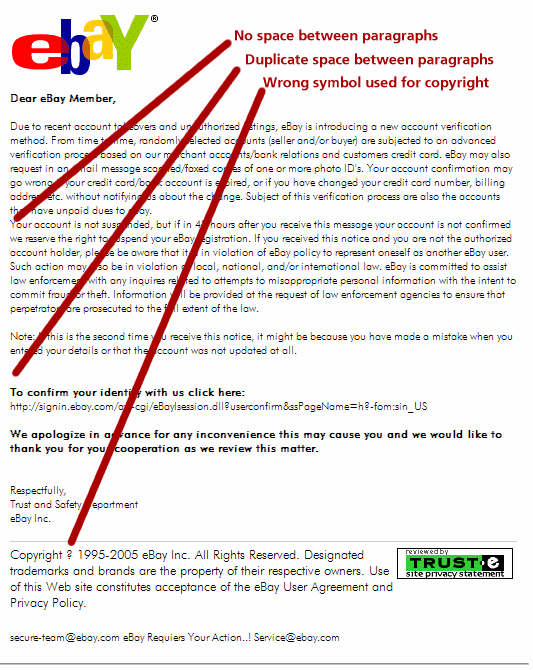
Warning Sign #2: Formatting Errors
Look closely at the layout of the page. As with the mechanical errors, these are not the sorts of errors that a professional service would be expected to make.
Warning Sign #3: Hidden Addresses and Sources
The original e-mail header appears below:
Received: from nobody by maleo.mydnsclient.com with local (Exim 4.44) id 1D9aTV-0003bc-C6Had the e-mail originated with eBay, the message would have come from an identifiable source at eBay.
Later -- and this is CRITICAL to recognizing phishing -- the address that appears in the body of the e-mail is not the same as the address that the reader will reach when he or she "clicks through":
To confirm your identity with us click here: < a href="http://209.50.231.168/~coba/auth[...truncated...]/" > http://signin.ebay.com/aw-cgi/eBayIsession.dll?userconfirm&ssPageName=h?-fom:sin_US < / a >The sender has used the trick of showing one address but using another. Unless the reader had carefully checked the source code of the email to ensure that the address he or she was visiting was the same as what was shown, he or she would probably never realize their mistake. Of course, the prevailing rule is that one should never respond to requests for confidential information sent by e-mail in the first place.
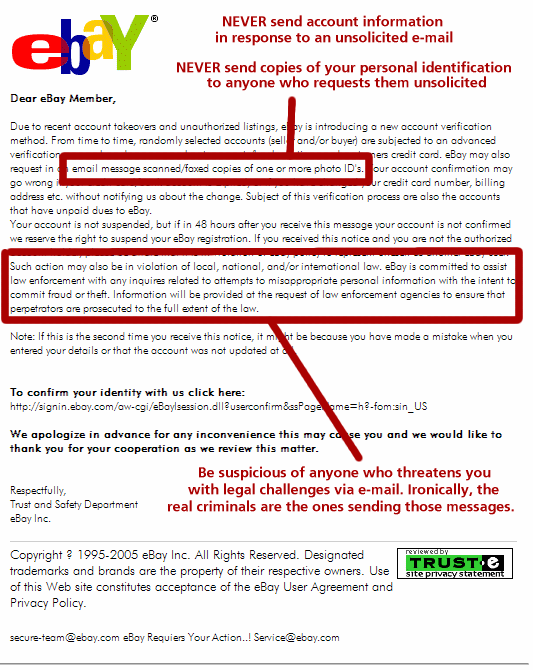
Warning Sign #4: Threatening You With Legal Mumbo-Jumbo
Read those threats carefully, then consider that they're being sent by someone who belongs in prison.
Report Phishing When You See It
For those who are comfortable doing so, it's important to try to report phishing attempts whenever possible. This helps law enforcement and prosecuting attorneys build a better case against the criminals. Many websites that the criminals are trying to exploit already have ways for users to report phishing. The eBay Security and Resolution Center offers such a method.
A side note: The eBay reporting system is too complicated. It requires the reporter to log-in, which is an unneccesary step and discourages people from reporting phishing.
Remember: Don't Respond to Requests for Private Information Via E-Mail
Bottom line: No reputable firm will ever request your confidential account information of any type via e-mail. If you think a request is legitimate, call the telephone number shown on a recent bill or account statement, or visit the company's home page (but not by clicking through from an e-mail -- type in the address yourself!) and use their contact page to find the right number to call.
